Breach Notification , Card Not Present Fraud , Fraud Management & Cybercrime
Trump Hotels Suffers Another Payment Card Breach
Sabre Breach Snares Trump Hotels, Plus Hard Rock Properties and Loews Hotels
Trump Hotels is warning customers that anyone who used a credit or debit card at 14 of its properties over a seven-month period may have had their card data compromised.
See Also: The Use Case of Machine Learning in Reducing Fraud for the Digital Banking Industry
The payment card data exposure represents the third serious data breach to have been suffered by the luxury hotel chain, which is based in New York, in as many years.
"We recently learned of an incident involving unauthorized access to guest information associated with certain hotel reservations," according to an undated, nine-page Trump Hotels breach notification. "This incident occurred on the systems of Sabre Hospitality Solutions (Sabre), a service provider used by Trump Hotels. It did not affect Trump Hotels' systems. The privacy and protection of our guests' information is a matter we take very seriously."
Travel industry software giant Sabre first sounded an alert in early May that its software-as-a-service SynXis Central Reservations system - used by more than 36,000 properties - was breached and payment card data and customers' personal details may have been stolen. The company hired incident response firm Mandiant to investigate.
Also affected by the Sabre breach were 21 Loews Hotels and 11 Hard Rock Hotel & Casino properties.
Seven-Month Breach
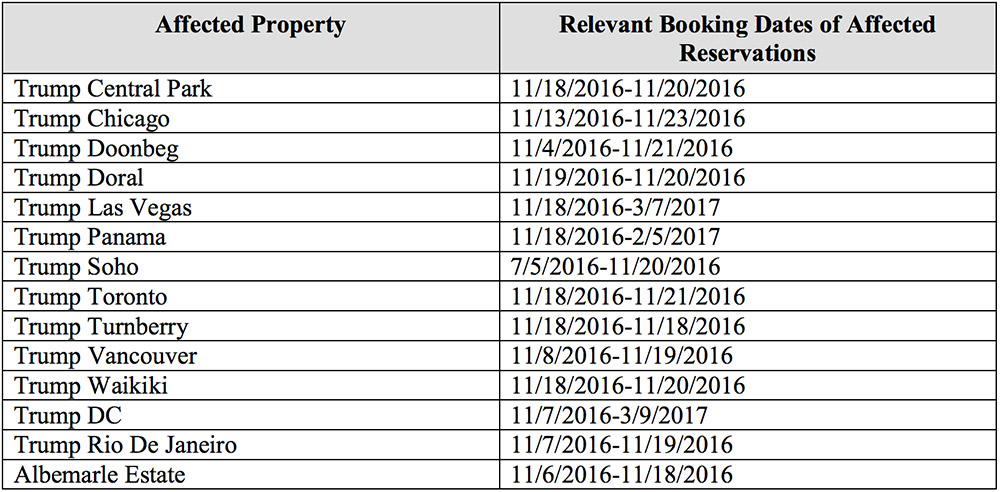
The notice from Trump International Hotels Management, aka the Trump Hotel Collection, says the hotel chain was first notified by Sabre on June 5 that 14 of its properties - ranging from hotels in Chicago and Las Vegas to Vancouver and Washington - were affected by the breach.
"The investigation found that the unauthorized party first obtained access to Trump Hotels-related payment card and other reservation information on August 10, 2016," the breach notification reads. "The last access to this information was on March 9."
Payment card data, including some security codes and cardholders' names - as well as contact information - were exposed. "Information such as Social Security, passport, and driver's license number was not accessed," the hotel chain says.
A link to the notification was posted on the Trump Hotels homepage via a discrete, one-line alert titled "notice regarding guest payment card information."
Trump Hotels Affected by the Sabre Breach
Reached for comment, a Trump Hotels spokeswoman declined to detail how many of its customers may have been affected, or why it waited for more than a month to warn customers about the breach.
"We take the privacy and protection of our guests' information very seriously, and we have provided notice to affected guests with recommended steps they can take to help protect against potential misuse of their information," the spokeswoman said.
Sabre Blames Outsider for Unauthorized Access
Sabre has blamed the breach of its SaaS system - used by travel agencies, hotels and booking services for such functions as rate and inventory management - on an intruder who managed to steal valid account-access credentials.
Sabre said information exposed in the breach included payment cardholder names, card numbers and expiration dates, and in some cases also security codes. Customers' names, phone numbers and addresses, among other personal details, were also potentially exposed.
Last week, Sabre declined to reveal to Information Security Media Group how many individuals or payment cards might have been compromised in the breach. Instead, Sabre spokesman Tim Enstice said that "less than 15 percent of the average daily bookings" using the reservation system were viewed during the seven-month breach, although he declined to say how many daily bookings are made, on average.
But Computerworld reports that Sabre's various software systems process 2 billion transactions per day, covering 1 billion unique travelers per year, which would mean that 300 million records may potentially have been exposed.
Sabre has disputed those estimates.
The breach was at least the second cybersecurity incident suffered by Sabre since 2015.
Other Trump Hotels Breaches
The Sabre-related breach alert by Trump Hotels follows the hotel chain in September 2015 warning that from May 19, 2014, until June 2, 2015, seven of its hotels had suffered a malware infection. At the time, Trump Hotels declined to tell Information Security Media Group how many payment card numbers or individuals might have been affected by the more than a year-long breach (see Trump Hotels Confirms POS Malware Breach).
Trump Hotels first learned of the May 2014 breach in June 2015, but it waited four months to alert customers, according to the office of New York's attorney general.
New York state investigators reported that Trump Hotels was again breached in November 2015, when an attacker gained access "installed credit card harvesting malware on 39 systems affecting five hotel properties including Trump SoHo New York."
In March 2016, meanwhile, the attacker returned, accessing a "legacy payment system" connected to the network of Trump International Hotel & Tower New York, which stored names and Social Security numbers for 302 people. THC issued a breach alert to victims about three months later.
Trump Hotels Fined For Slow Notification
The hotel chain's decision to wait months before alerting customers to the breach that began in May 2014 drew a strong rebuke from New York state regulators, including a fine (see Data Breach Notifications: What's Optimal Timing?).
On September 23, 2016, Eric T. Schneiderman, New York's attorney general, announced that Trump International Hotels Management had agreed to pay $50,000 in penalties as well as implement more robust information security practices, including two-factor authentication. Schneiderman's office said that the breaches had collectively led to the compromise of than 70,000 payment card details as well as the 302 social security numbers.
"It is vital in this digital age that companies take all precautions to ensure that consumer information is protected, and that if a data breach occurs, it is reported promptly to our office, in accordance with state law," Schneiderman said in a statement at the time.
Hospitality Sector Breach Epidemic
Trump Hotels, Hard Rock and Loews Hotels are far from the only hotel chains to be targeted by attackers.
"Why are hackers targeting hotels? Well, because they're a good target," Peter W. Singer, a senior fellow at think tank New America Foundation, tells the Washington Post. "Then you look at Trump's hotels, and they're obviously a highly symbolic target."
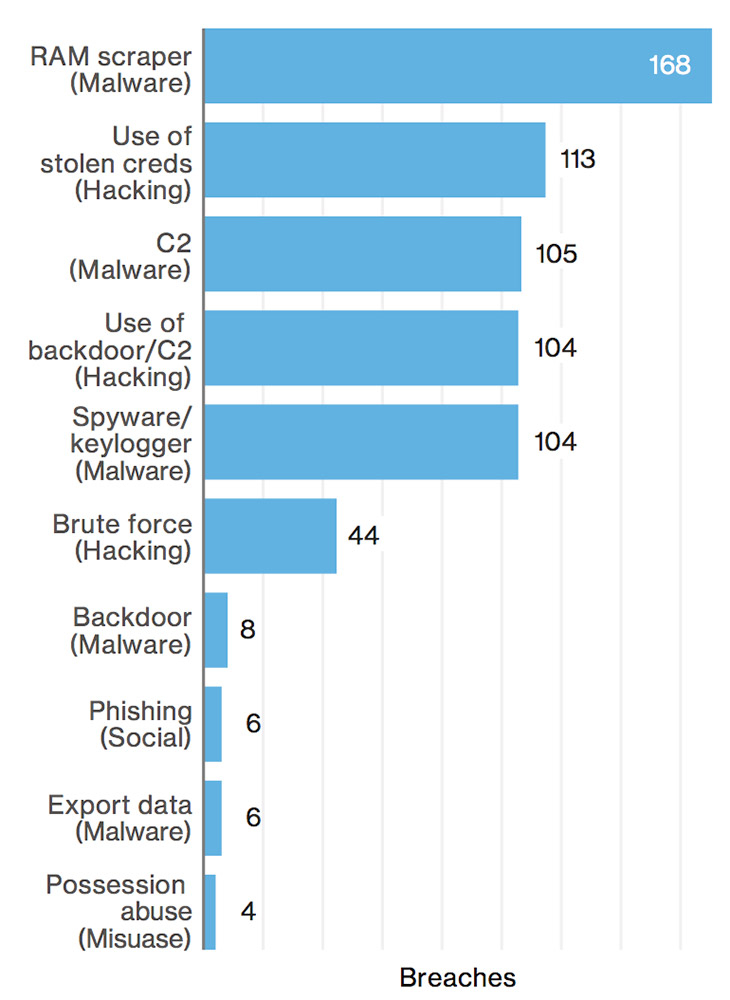
Verizon's 2017 Data Breach Investigations Report found that 96 percent of all hospitality sector breaches - including hotels and restaurants - involved payment card data. Such data can be resold on underground forums as well as monetized via money mules making fraudulent purchases or ATM withdrawals.
The hospitality sector breach epidemic is compounded by too many such organizations failing to prepare for breaches or put in place proper detection and response capabilities, according to Verizon.
In April, Intercontinental Hotels Group warned that malware had infected POS devices at 1,200 of its locations - including Crowne Plaza, Intercontinental, Kimpton and Holiday Inn properties - beginning in September 2016. Other hotels that have been breached have included HEI Hotels & Resorts - which manages some hotels owned by IHG - as well as Hilton, Hyatt, Omni Hotels & Resorts and Starwood Hotels and Resorts, among others.
In addition to Sabre, several other third-party vendors have also been breached. That included Oracle, which in August of last year warned that an attacker planted malware in a support portal for servicing and maintaining its MICROS POS systems - one of the mostly widely used POS systems in the world, with 330,000 customers in 180 countries.






















